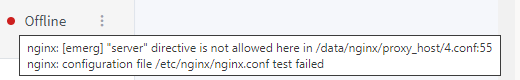
DocFraggle Rightio, lots of progress but still not quite right.
To solve the 502 gateway error because I had not put my proxy network in the Mailcow docker-compose file as some people recommended/suggested I change the HTTP and HTTPS port binds in the mailcow.conf file to the local IP address of my docker server (192.168.50.250).
I also configured on the Nginx reverse proxy Forward Hostname/IP to also be the local IP address of the Docker server and lastly on the advanced configuration to also use the local IP instead of the loopback address.
This bit here is where it all goes downhill and goes offline.
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name CHANGE_TO_MAILCOW_HOSTNAME autodiscover.* autoconfig.;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name CHANGE_TO_MAILCOW_HOSTNAME autodiscover. autoconfig.*;
ssl_certificate MAILCOW_PATH/data/assets/ssl/cert.pem;
ssl_certificate_key MAILCOW_PATH/data/assets/ssl/key.pem;
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:50m;
ssl_session_tickets off;
See for the latest ssl settings recommendations
An example config is given below
ssl_protocols TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5:!SHA1:!kRSA;
ssl_prefer_server_ciphers off;
I even tried modify the one from here but still failed:
server {
listen 80 default_server;
listen [::]:80 default_server;
location / {
return 301 https://$host$request_uri;
}}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
ssl_certificate /path/to/signed_cert_plus_intermediates;
ssl_certificate_key /path/to/private_key;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:10m; # about 40000 sessions
ssl_session_tickets off;
# curl https://ssl-config.mozilla.org/ffdhe2048.txt > /path/to/dhparam
ssl_dhparam /path/to/dhparam;
# intermediate configuration
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305;
ssl_prefer_server_ciphers off;
# HSTS (ngx_http_headers_module is required) (63072000 seconds)
add_header Strict-Transport-Security "max-age=63072000" always;
# OCSP stapling
ssl_stapling on;
ssl_stapling_verify on;
# verify chain of trust of OCSP response using Root CA and Intermediate certs
ssl_trusted_certificate /path/to/root_CA_cert_plus_intermediates;
# replace with the IP address of your resolver
resolver 127.0.0.1;}