I have pretty much the same issue and somehow cannot get it to run properly. Mailcow is behind an NGINX Proxy Manager that are hosted on different VM´S. I´m having troubles with connecting Mac OS Clients with autodiscover. Would there be anybody offering a paid screen sharing session to fix this installation ? thanks in advance, Frank

EnglishNginx Reverse proxy configuration
So if I just have this configuration in the advanced tab I get a 502 bad gateway but my host at least shows online in Nginx.
location /Microsoft-Server-ActiveSync {
proxy_pass http://127.0.0.1:8080/Microsoft-Server-ActiveSync;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_connect_timeout 75;
proxy_send_timeout 3650;
proxy_read_timeout 3650;
proxy_buffers 64 512k; # Needed since the 2022-04 Update for SOGo
client_body_buffer_size 512k;
client_max_body_size 0;
}
location / {
proxy_pass http://127.0.0.1:8080/;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
client_max_body_size 0;
The following Proxy Buffers has to be set if you want to use SOGo after the 2022-04 (April 2022) Update
Otherwise a Login will fail like this: mailcow/mailcow-dockerized4537
proxy_buffer_size 128k;
proxy_buffers 64 512k;
proxy_busy_buffers_size 512k;
}
But if I added the full recommended Advanced config the host shows offline and I get a SSL_ERROR_UNRECOGNIZED_NAME_ALERT on the web page.
If I go to the IP and port of the mail server both HTTP (8080) and HTTPS (8443) it works and the SSL certificate shows correctly as valid and issued to the mail server domain name. I copied the SSL cert and key from Nginx Proxy into the Mailcow SSL folder so it is ready the SSL certificate correct.
There is a Logs folder in the nginx/data folder but all the files in there are blank. The audit logs page on the Nginx dashboard is just showing when I have made a change to a host.
even adding just this section in causes the host to go offline.
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name CHANGE_TO_MAILCOW_HOSTNAME autodiscover.* autoconfig.;
return 301 https://$host$request_uri;
}
DocFraggle Rightio, lots of progress but still not quite right.
To solve the 502 gateway error because I had not put my proxy network in the Mailcow docker-compose file as some people recommended/suggested I change the HTTP and HTTPS port binds in the mailcow.conf file to the local IP address of my docker server (192.168.50.250).
I also configured on the Nginx reverse proxy Forward Hostname/IP to also be the local IP address of the Docker server and lastly on the advanced configuration to also use the local IP instead of the loopback address.
This bit here is where it all goes downhill and goes offline.
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name CHANGE_TO_MAILCOW_HOSTNAME autodiscover.* autoconfig.;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name CHANGE_TO_MAILCOW_HOSTNAME autodiscover. autoconfig.*;
ssl_certificate MAILCOW_PATH/data/assets/ssl/cert.pem;
ssl_certificate_key MAILCOW_PATH/data/assets/ssl/key.pem;
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:50m;
ssl_session_tickets off;
See for the latest ssl settings recommendations
An example config is given below
ssl_protocols TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5:!SHA1:!kRSA;
ssl_prefer_server_ciphers off;
I even tried modify the one from here but still failed:
server {
listen 80 default_server;
listen [::]:80 default_server;
location / {
return 301 https://$host$request_uri;
}}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
ssl_certificate /path/to/signed_cert_plus_intermediates;
ssl_certificate_key /path/to/private_key;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:10m; # about 40000 sessions
ssl_session_tickets off;
# curl https://ssl-config.mozilla.org/ffdhe2048.txt > /path/to/dhparam
ssl_dhparam /path/to/dhparam;
# intermediate configuration
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305;
ssl_prefer_server_ciphers off;
# HSTS (ngx_http_headers_module is required) (63072000 seconds)
add_header Strict-Transport-Security "max-age=63072000" always;
# OCSP stapling
ssl_stapling on;
ssl_stapling_verify on;
# verify chain of trust of OCSP response using Root CA and Intermediate certs
ssl_trusted_certificate /path/to/root_CA_cert_plus_intermediates;
# replace with the IP address of your resolver
resolver 127.0.0.1;}
Dumb question, but you did change stuff like
MAILCOW_PATH/data/assets/ssl/cert.pem
or
CHANGE_TO_MAILCOW_HOSTNAME
to the correct path and hostname, right?
DocFraggle I work in IT mate, stuff like that is never a dumb question to ask lol
so the full location from my home directory is docker_volumes/mailcow-dockerized/data/assets/ssl/cert.pem and I have manually copied the cert.pem and key.pem from Nginx to this location. I have disabled Mailcow from being able to get its own SSL certificate in the mailcow.conf file by changing this line SKIP_LETS_ENCRYPT=y
I have got autodiscovery working (mostly) exchange activesync works but IMAPS does not work (I have port 25, 587,465 993 and 4190 ported forward to my docker server for Mailcow plus 80 and 443 for Nginx itself.
The bit I am unsure of for that section is the Mailcow path itself, do I start its location from the home directory or from the Nginx folder or the Mailcow folder.
I added mail.domain.com autodiscover.domain.com and autoconfig.domain.com to the advanced configuration, the let’s encrypt SSL certificate, and to the proxy host domains section (I am a HUGE dumbarse and should have realised adding all 3 subdomains was necessary…)
Rightio, I am making good progress I believe.
I solved the IMAPS issue, I had the port forward wrong, this is all I will say on this matter…..
When I put in the full, filled-out version of the Nginx advanced configuration for Mailcow it knocks it offline as we all know but what I didn’t know is you can hover your mouse over the offline area and it will give you a sippet of what is causing the error.
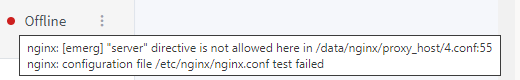
Doing a bit more searching I am still stumped on how to fix it though.
- Best Answerset by EverythingBySam
Rightio, so here is everything I have learned!
This is everything you need to configure in the Advanced tab (adjust the IP and port according to your setup for both locations.) Everything else above this from the Mailcow website is already configured elsewhere in Nginx Reverse Proxy so you are doubling up and causing issues if you try to use it. Well done to @DocFraggle for giving me the complete answer without me realising.
location /Microsoft-Server-ActiveSync {
proxy_pass http://127.0.0.1:8080/Microsoft-Server-ActiveSync;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_connect_timeout 75;
proxy_send_timeout 3650;
proxy_read_timeout 3650;
proxy_buffers 64 512k; # Needed since the 2022-04 Update for SOGo
client_body_buffer_size 512k;
client_max_body_size 0;
}
location / {
proxy_pass http://127.0.0.1:8080/;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
client_max_body_size 0;
The following Proxy Buffers has to be set if you want to use SOGo after the 2022-04 (April 2022) Update
Otherwise a Login will fail like this: mailcow/mailcow-dockerized4537
proxy_buffer_size 128k;
proxy_buffers 64 512k;
proxy_busy_buffers_size 512k;
}
Port any other ports you need for mail server 25, 465, 587, 993, 4190, etc to the IP of docker host.
make sure you add all 3 hostnames (mail.domain.com, autodiscover.domain.com and autoconfig.domain.com) to the domains names section on your Nginx reverse proxy host as well as on the SSL certificate tab.
You will need to download the SSL certificate, copy it to YOUR_MAILCOW_PATH//data/assets/ssl/ and rename the cert and key file to cert.pem and key.pem then restart your container. You will need to copy the new certificate every 3 months to this location manually, I have not figured out a way do get the ACME request to work through proxy.
I hope this helps someone! Huge shoutout to @DocFraggle especially for his persistence and patience!
If anyone has any ideas how to maybe get the certificate request to work, let me know and we might be able to work it out together.
- Edited
Good to hear!
And eventually you will learn to paste config files and logs with the “code” markdown </> for better readability 
If anyone has any ideas how to maybe get the certificate request to work,
If you use a reverse proxy, you need to always get the certificates on the reverse proxy and copy them over. I do this with ansible (which runs after the certificates have been renewed), and ansible also restarts the 3 services.
esackbauer Ah is that how you do it, thank you. Sorry I am not really a forum type person most of the time I just search the entire internet in silence.
So Ansible does it automatically or does it require manual intervention?
I will look into it as I would like to do a complete guide to help others who don’t quite understand just like I was.
EverythingBySam So Ansible does it automatically or does it require manual intervention?
It depends  you could totally automate it with Ansible. However you need to learn it.
you could totally automate it with Ansible. However you need to learn it.
esackbauer I am always up for learning something useful which why I didn’t give up on this and ended up learning how the whole Nginx proxy worked.
Looks like I have a busy weekend ahead
Thanks for the suggestion and link.
- Edited
Hello everyone,
What a great project mailcow, thank you very much for it. But I’m still failing with the setup.
I have also successfully installed mailcow in a VM. All containers are running without errors. But I also have an NPM Nginx Proxy Manager running in another VM like here.
I have now proceeded as described here in the article. Then I get a “502 Bad Gateway” when I want accessing the mailcow login. The access is then not visible in the Mailcow log.
If I leave the ports in mailcow.conf at default and do not bind it to 127.0.0.1, and delete the entries on the advanced tab in NPM I at least get a “403 forbidden” and the access can be seen in mailcow.conf with the IP of the NPM with “permission denied”
Does anyone have an idea what I am doing wrong?
How should the forwarding in the NPM look like? I currently have https set to IP:8443.
Oh and I have deactivated certificates in mailcow, I would like to do this via the NPM.
Thank for any help…..
- Edited
These 2 are contradicting. If you leave the mailcow ports at default (which is OK if you run NPM and mailcow on different VMs), then you need to forward from NPM to Mailcow VMs IP address on port 443 of course.
Regarding certificates, you need to copy the fullchain.pem and privkey.key to mailcow VM as described here:
- Edited
Thank you for your fast answer.
Ok I have now do the following:
- mailcow.conf standard, Port 80/443 and no IP bind
- NPM: delete the entries on advanced tab as in the thread above describes and forward to VM-IP:443
I recieve now “403 Forbidden” and “Permission denied” in the log of mailcow. The permission denied is about the IP from the NPM…..
Something doesn’t fit and I don’t know what or where. Mailcow does not allow my NPM to access it.
I understood about the certificate, thank you. But I can do that in the end, right? Not until the 403 problem is solved?
- Edited
I don’t understand correctly. Do I have to log in for Fail2Ban? I can’t log in because the page says 403 Forbidden. Can I just stop the Netfilter container? I also have Fail2Ban in the operating system but that stopped.
mailer I also have Fail2Ban in the operating system
Please don’t do this in the mailcow VM, you are adding error sources. Mailcow has already Netfilter/fail2ban function built in. Remove the fail2ban altogether and leave that job for mailcow itself or your NPM.
In the Netfilter page in your mailcow UI you should see who is blocked. I have a similar setup as you have, I have whitelisted the IP address of my reverse proxy in netfilter.
Try first to publish mailcow without the NPM, directly with SNAT rule, and then check Netfilter settings
I removed fail2ban completely with apt purge. But it was also stopped beforehand. It didn’t change anything. Still 403 forbidden.
I don’t know how to configure access without NPM, can you describe it in more detail? Do you mean access directly with in the browser? Sorry I am not really an expert at the moment.
- Edited
Ok then I understood it correctly and I also tested access via the IP beforehand. There is always the 403 forbidden error and a “Permission denied” entry in the mailcow nginx container. If I want direct access, do I have to change anything in mailcow.conf?



