I guess its MUCH easier to run Mailcow in a Proxmox VM with debian and docker. There is almost no overhead, as Debians footprint is quite small if you install it without GUI.

English[HOWTO] Install mailcow in a LXC container on Proxmox 6.4-13 for home usage
@esackbauer yes i agree with this and if vm use ceph as starage we could gain HA options
aukfood On Proxmox you don’t need Ceph, you can use either ZFS replications or the inbuilt
@esackbauer i don’t try again zfs replications but why not
Hi all,
Just migrate my old Proxmox 6.x to the new version 8.0.3.
Backup the Proxmox VM (CT) and restore on the new Proxmox.
It works like a charmn, without any preparation on the new Proxmox (Overlay and Naufs) just restore and run.
So now, you can at least skip the first step “I - Prepare your proxmox hypervisor”
esackbauer I guess its MUCH easier to run Mailcow in a Proxmox VM with debian and docker. There is almost no overhead, as Debians footprint is quite small if you install it without GUI.
Good day, I’m new to mailcow, so this is my first post/question.
Here’s my setup:
one static IP –> opnsense –> proxmox –> debian 12 as VM –> mailcow-dockerized. The opnsense, proxmox and debian VM are in the same subnet. On the proxmox is running a not containerized server, also in the same subnet. No firewall(s) on the proxmox.
Install of debian 12 went smooth, the VM is up and running. Same with mailcow-dockerized, no problems so far. mailcow is connected to a domain, DNS records are set as described. mailcow is able to send and receive email.
During acme-challenge the static IP is detected, but it stalls with the hostname. No cert is created, BTW the server in the other machine has no problem with let’s encrypt certs. Difference for sure is docker.
I’m not firm with docker. But if I’m guided I’m able to provide any information to work this through. I’ve access to the opnsense and to the network over VPN.
So while reading the intro of mailcow that installations in a VM are supported or possible, where did I miss the point? I tried to get information in opnsense- and proxmox-forum but I must admit, the more I read the more I’m confused. I also read the mailcow docs, but I simply don’t understand where do I have to investigate. Is it the opnsense part or is it the mailcow part, or both?
Any help would be greatly appreciated.
regards, stefan
- Edited
stefan21 BTW the server in the other machine has no problem with let’s encrypt certs.
That seems the problem. You need to NAT all ports in this list to the mailcow VM:
The Acme challence for mailcow certs cannot work if port 80 goes to another server.
So you are better off to disable Acme in mailcow and use a proper which handles all certificates for all your VMs.
Configure mailcow for reverse proxy:
Then you need to copy the certificates from that reverse proxy to the mailcow VM:
Yes, esackbauer is right !
My certificate was renewed with the ACME challenge by my NAS (Port 80/433 routed on it).
I made a script to copy the generated certificate each night to my mailcow server (reboot it also to take the new certificate).
Works well since months !
First I’d like to thank for taking the time to reply to my questions.
I understand the easy advice as follows:
- in opnsense I install the acme plugin and let the opnsense take care for the let’s encrypt certs. I already tested this way, this plugin works.
- I daily copy, preferably with a cron job, the certs to mailcow - what path/location exactly?
- the mailcow VM has to be daily rebooted, to recognize the new certs?
Thank you for describing the way with a reverse proxy. I tried this but honestly, as a part time admin, this is way too complicated for me.
Everything works really pretty well out of the box, if mailcow does not sit in a VM (and probably in lxc container) and behind a firewall like opnsense or pfsense. I tested mailcow at home on a laptop running with arch linux. There’s an asus router in front of the home network. No problem to configure a port forward to the laptop, so everything works as intended.
Anyway, if I take the road kicou suggests, where in mailcow can acme be safely disabled? Is it in the GUI or better with the command line?
stefan21 what path/location exactly?
mailcow VM has to be daily rebooted, to recognize the new certs?
All your questions are already answered in the last link of my previous posting…
My script on the NAS (Auth by key) :
#!/bin/bash
scp -i /root/.ssh/id_rsa /usr/syno/etc/certificate/archive/hkbWEi/fullchain.pem root@192.168.0.3:/root
scp -i /root/.ssh/id_rsa /usr/syno/etc/certificate/archive/hkbWEi/privkey.pem root@192.168.0.3:/root
My daily cron script on mailcow server :
#!/bin/sh
copy cert to data folder
cp -f /root/fullchain.pem /opt/mailcow-dockerized/data/assets/ssl/cert.pem
cp -f /root/privkey.pem /opt/mailcow-dockerized/data/assets/ssl/key.pem
rm -f /root/fullchain.pem
rm -f /root/privkey.pem
restart needed docker
docker restart $(docker ps -qaf name=postfix-mailcow)
docker restart $(docker ps -qaf name=nginx-mailcow)
docker restart $(docker ps -qaf name=dovecot-mailcow)
Doing this daily seems unnecessary. Certs are good for 90 days with renewal possible after 60.
I run a script on mailcow instance itself to check renewal weekly using dns challenge (cloudflare) as I don’t want any more open ports than absolutely necessary. Dns challenge requires the use of an api key to update the require txt record.
I managed to fetch certs with opnsense acme-plugin. Already tested, works fine. I also managed to automate the deploy of the cert to mailcow. In the mailcow-docs is said:
"How to use your own certificate¶
Make sure you disable mailcows internal LE client (see above).
To use your own certificates, just save the combined certificate (containing the certificate and intermediate CA/CA if any) to data/assets/ssl/cert.pem and the corresponding key to data/assets/ssl/key.pem"
The copy of the certs from the opnsense is in:
/opt/mailcow-dockerized/data/assets/ssl/FQHN/
- ca.pem
- cert.pem
- fullchain.pem
- key.pem
Will that work?
It won’t. No problem to write a cron job.
Some other questions are popping up:
In the doc I read: "Die mailcow Daten (wie bspw. E-Mails, Userdaten etc.) werden in Docker-Volumes aufbewahrt - geben Sie gut auf diese Volumes acht:
clamd-db-vol-1
crypt-vol-1
mysql-socket-vol-1
mysql-vol-1
postfix-vol-1
redis-vol-1
rspamd-vol-1
sogo-userdata-backup-vol-1
sogo-web-vol-1
solr-vol-1
vmail-index-vol-1
vmail-vol-1"
O.k. Got it. Are those volumes covered within the backup-script?
While I’m migrating from another email-server, is it possible to upload bulk white/black lists?
- Edited
Friends, I have to ask you for help. mailcow is behind nginx proxy manager on 192.168.12.15, mailcow address is 192.168.12.41. It runs on mail.example.com the interface works, but when you start docker compose upd, an error pops up: Your hands are already dropping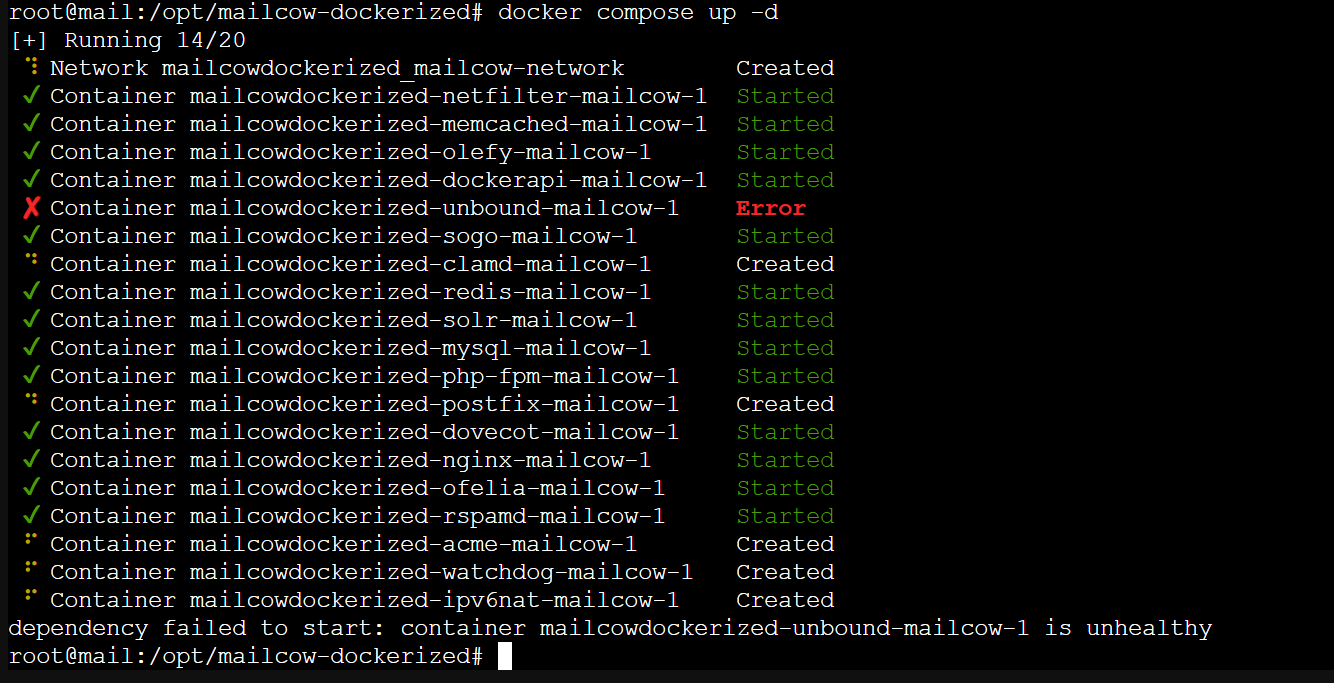
[unknown] Any help is greatly appreciated
Hi
Really its not needed to prepare Proxmox host form MailCow LXC?
- Edited
KrisFromFuture prepare Proxmox host form MailCow LXC?
“Do not try to install mailcow on a Synology/QNAP device (any NAS), OpenVZ, LXC or other container platforms.”



