Hello everyone
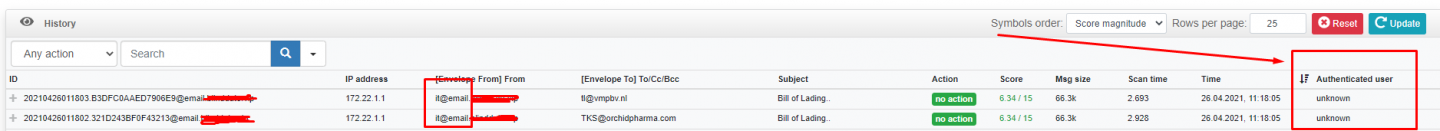
I’ve to install mailcow mail server some month ago. Everything works well but today I got a message from my VPS provider that my mail server suspended due to spam activity. It was a spam activity from nonauthorized user from my mail domain.
All spam messages were sent from “it@email.mydomain.com”
I have set my DNS and DKIM, DMARC, SPF like:email.mydomain.com as mailcow Web Interface and mydomain.com as mail domain
so my DNS config looks:
I created “A” record with “email” and IP
“CNAME” with “autoconfig” and “email.mydomain.com”
“CNAME” with “ autodiscover” and “email.mydomain.com”
“MX” with @ and “email.mydomain.com” (Priority: 20)
“TXT” with @ and “=spf1 mx a -all”
DKIM with my key
“DMARC” v=DMARC1; p=quarantine;
So guys can you help and give some advice on what I did wrong when setting mail server or where my mail serve was hacked by spamers?
I have never created this email user “it@email.mydomain.com” and right now it doesn’t exist on my mail server.
Although “email.mydomain.com” is not a mail domain it just a web interface from my mail server. My mail domain is just “mydomain.com” without subdomain
I use mailcow docker-compose as mail server and ubuntu 20.04 with Nginx as reverse-proxy