I contacted the Hetzner support and they told me that there is only a limitation for cloud servers (see https://docs.hetzner.com/cloud/servers/faq/#why-can-i-not-send-any-mails-from-my-server) which can be disabled after a while. Anyway, I’m using a dedicated server and there is no SMTP filtering.
Trying manually to connect to a MX server, where the Mailcow Postfix is not able to connect, shows no issues:
root@mail01:~# openssl s_client -starttls smtp -connect mx-ha03.web.de:25 -crlf -ign_eof
CONNECTED(00000003)
depth=2 C = DE, O = T-Systems Enterprise Services GmbH, OU = T-Systems Trust Center, CN = T-TeleSec GlobalRoot Class 2
verify return:1
depth=1 C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
verify return:1
depth=0 C = DE, ST = Rheinland-Pfalz, L = Montabaur, O = 1&1 Mail & Media GmbH, CN = mx.web.de
verify return:1
---
Certificate chain
0 s:C = DE, ST = Rheinland-Pfalz, L = Montabaur, O = 1&1 Mail & Media GmbH, CN = mx.web.de
i:C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
a:PKEY: rsaEncryption, 3072 (bit); sigalg: RSA-SHA256
v:NotBefore: Feb 19 07:05:18 2025 GMT; NotAfter: Feb 23 23:59:59 2026 GMT
1 s:C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
i:C = DE, O = T-Systems Enterprise Services GmbH, OU = T-Systems Trust Center, CN = T-TeleSec GlobalRoot Class 2
a:PKEY: rsaEncryption, 3072 (bit); sigalg: RSA-SHA256
v:NotBefore: Aug 2 09:16:44 2022 GMT; NotAfter: Aug 2 23:59:59 2027 GMT
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIJBTCCB22gAwIBAgIQOZrsxtVRqfTT7SgrKcgxOTANBgkqhkiG9w0BAQsFADBo
MQswCQYDVQQGEwJERTEnMCUGA1UECgweRGV1dHNjaGUgVGVsZWtvbSBTZWN1cml0
eSBHbWJIMTAwLgYDVQQDDCdUZWxla29tIFNlY3VyaXR5IFNlcnZlcklEIE9WIENs
YXNzIDIgQ0EwHhcNMjUwMjE5MDcwNTE4WhcNMjYwMjIzMjM1OTU5WjBvMQswCQYD
VQQGEwJERTEYMBYGA1UECBMPUmhlaW5sYW5kLVBmYWx6MRIwEAYDVQQHEwlNb250
YWJhdXIxHjAcBgNVBAoMFTEmMSBNYWlsICYgTWVkaWEgR21iSDESMBAGA1UEAxMJ
bXgud2ViLmRlMIIBojANBgkqhkiG9w0BAQEFAAOCAY8AMIIBigKCAYEA1Rk5R3tz
9VvUrtiSqwHqz1lcfY+nv99+QjzLy/PRta8jQGapToY7WREcN0EO8L8uTbqFARqt
t4YXW+dSYpzQxz/zkAfrzPecpkPLc08xPfyY3p3CdWDT6Bb8KvyfD/uhW/mRVjd2
9rsHgcdtnkfHwYJCcBSCG/VK9+pPQmh9Pg9T8I+OwJ9i3WD8s6Wnzw6u38l9Ld1L
qvgVh8TeKVdB4elzf5BfCOIU5TbOq0+Tphk22B4vvgSrwtb1R0cDvgsxRHclG57q
PgMhig4RUtz0a1BXNLIaHTTEMue4KxmTRJwuYsYvbDIxNBGPjRpQeG/wwLbVmMzX
mm1RnmuSStHX+vQsgF9Yh/GZECKr3qF7z49JgqMzLqdugO6NPu8V4Ub8+KE9MUOs
4q/TfteNZwYcC9W7chatY0RIm+Vg0+1kD6wIP/BFYzPWiC75tVoOb9EiCnZuqrp2
FhojFEu0jZ63SBNmArq6fTfUEegfr4i8QYrU3Q6SN+Pd9msYcOuLEvs/AgMBAAGj
ggSiMIIEnjAfBgNVHSMEGDAWgBQcBZOxf6g0MIxS4JZAoHKjEF3g/zAOBgNVHQ8B
Af8EBAMCBaAwHQYDVR0lBBYwFAYIKwYBBQUHAwIGCCsGAQUFBwMBMB0GA1UdDgQW
BBTNC9rCOuJsRiwy4JSbl9JvicnXcTBTBgNVHSAETDBKMEgGBmeBDAECAjA+MDwG
CCsGAQUFBwIBFjBodHRwOi8vZG9jcy5zZXJ2ZXJpZC50ZWxlc2VjLmRlL2Nwcy9z
ZXJ2ZXJpZC5odG0wXgYDVR0fBFcwVTBToFGgT4ZNaHR0cDovL2NybC5zZXJ2ZXJp
ZC50ZWxlc2VjLmRlL3JsL1RlbGVrb21fU2VjdXJpdHlfU2VydmVySURfT1ZfQ2xh
c3NfMl9DQS5jcmwwgZ8GCCsGAQUFBwEBBIGSMIGPMDEGCCsGAQUFBzABhiVodHRw
Oi8vb2NzcC5zZXJ2ZXJpZC50ZWxlc2VjLmRlL29jc3ByMFoGCCsGAQUFBzAChk5o
dHRwOi8vY3J0LnNlcnZlcmlkLnRlbGVzZWMuZGUvY3J0L1RlbGVrb21fU2VjdXJp
dHlfU2VydmVySURfT1ZfQ2xhc3NfMl9DQS5jcnQwDAYDVR0TAQH/BAIwADBSBgNV
HREESzBJgglteC53ZWIuZGWCDm14LWhhMDIud2ViLmRlgg5teC1oYTAzLndlYi5k
ZYINZGhteDAxLndlYi5kZYINZGhteDAyLndlYi5kZTCCAnIGCisGAQQB1nkCBAIE
ggJiBIICXgJcAHYADleUvPOuqT4zGyyZB7P3kN+bwj1xMiXdIaklrGHFTiEAAAGV
HQaBvAAABAMARzBFAiEAz3VK7RGd3IKfHanmc/bKtQ2QjmEy0WPgxSEEDJniM/cC
IF8GsCm+cqOypLozUQeZDfsI9tHq6CeKv215cOXl8dSoAHcAlpdkv1VYl633Q4do
NwhCd+nwOtX2pPM2bkakPw/KqcYAAAGVHQaEhgAABAMASDBGAiEAts5WxxOZu8WK
fu7IxMqBfTj/sv/Vw/NQAWaX+fPTS0ACIQD/Gf740GA9ald0ikhfzSlkzIkOAWM9
OGzWzLQ5iGrnNwB3ABmG1Mcoqm/+ugNveCpNAZGqzi1yMQ+uzl1wQS0lTMfUAAAB
lR0GgNIAAAQDAEgwRgIhAJUqplDG2Rtum04Ij/9lA+KI7RcQMTnLauP/0Z+F9yFg
AiEA+gtSPraNeWaEfa+HLMkaR6pYRpZRoUFQWHX4bpVvJncAdwBJnJtp3h187Pw2
3s2HZKa4W68Kh4AZ0VVS++nrKd34wwAAAZUdBoDhAAAEAwBIMEYCIQDtDZaKzsel
5DJ4viCX5w6rMlWp7PlmHOcAvTTtUOBxxgIhAIdLeWNvydLQlhmYrAo5P+bzim42
IxGEYt12XUpwGynSAHcAZBHEbKQS7KeJHKICLgC8q08oB9QeNSer6v7VA8l9zfAA
AAGVHQaBhQAABAMASDBGAiEA+DAX2eoGZV0NGZ8x2vSvqjd8zAA4gWupOAIwH9jj
hwICIQDvw3ZDzaDNEcm5337zg3UCuzeaP0b98uGeTNsmnu8HPTANBgkqhkiG9w0B
AQsFAAOCAYEAvfDcT2aZLqTkuFX+8xXo8CxGPFrGxK5N4nKME7jQqrNcHuyoK38D
uVezri4kAL3xXXygJzVumqy9Lmaw0PRx6kewNqfWQJpfHbnQpr5f757te3vEek1c
9/MqEuN931XtkrqN6+K646WHzc4UZW5fvtDi/8m+svv2R+Gu9HfpI4yt2TMX7p8I
cB8M5nG4Qu8jpi1i5RCUXV9mfKDHC+ki/M+gf8DnVKJQNWNuV+AEfi7SksJbUrvd
+6DTe1gB0D5F7ArbOJ6TP6aywlEm86iRURz/DMh8QO5ZUWSoMcyf3SGOET7YD8ha
8uAgyq5vIzCsy8a5rs4hsCQI/Ug1jTERZJLUGf1T2pIPjrZRpO6Bw3yJLL8CByM+
2mQXy4Gy4wex13IAGXoqyFY4cpkqet301k0jeo7kKVf98+dRXO/8d7gR6i5Y/cWT
pzMxy8OKRQUek9UlufA9WWIAG2f1S1cmeKakg3ciUcJj3I1I+4LD9W9lnlRcZ8UN
AtGtV889D5M5
-----END CERTIFICATE-----
subject=C = DE, ST = Rheinland-Pfalz, L = Montabaur, O = 1&1 Mail & Media GmbH, CN = mx.web.de
issuer=C = DE, O = Deutsche Telekom Security GmbH, CN = Telekom Security ServerID OV Class 2 CA
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: ECDH, prime256v1, 256 bits
---
SSL handshake has read 4686 bytes and written 786 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 3072 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
250 STARTTLS
Here the log entries of the Mailcow Postfix log when trying to connect to the exact same server:
postfix-mailcow-1 | Sep 25 10:57:27 9f3f2b5235f7 postfix/smtp[430]: SSL_connect error to mx-ha03.web.de[212.227.15.17]:25: Connection timed out
postfix-mailcow-1 | Sep 25 10:57:27 9f3f2b5235f7 postfix/smtp[430]: DDAE51403F4: to=<redacted-for-pricavy@web.de>, relay=mx-ha03.web.de[212.227.15.17]:25, delay=601, delays=0.6/0/600/0, dsn=4.7.5, status=deferred (Cannot start TLS: handshake failure)
I checked the TLS version and ciphers and found no issue.
The TLS policies are empty and TLS is not enforced in the settings of any user:
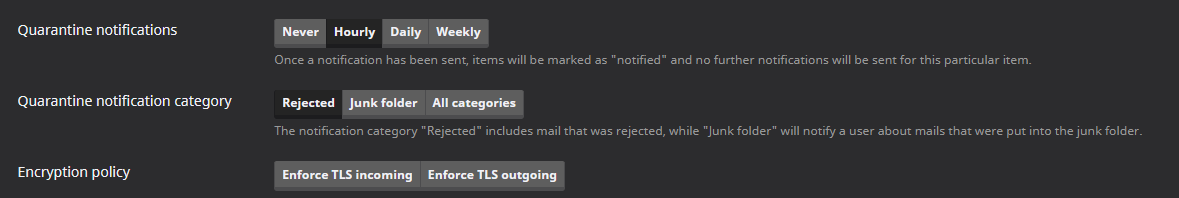
When searching for smtp_tls_policy_maps, there is no place where something is set, except for the lookup in the database, which returns no results:
root@mail01:~# grep -R "smtp_tls_policy_maps" /opt/mailcow-dockerized/
/opt/mailcow-dockerized/update_diffs/diff_before_update_2025-09-25-10-43-27:+smtp_tls_policy_maps =
/opt/mailcow-dockerized/data/conf/postfix/extra.cf:# smtp_tls_policy_maps =
/opt/mailcow-dockerized/data/conf/postfix/main.cf: $smtp_tls_policy_maps,
/opt/mailcow-dockerized/data/conf/postfix/main.cf:smtp_tls_policy_maps = proxy:mysql:/opt/postfix/conf/sql/mysql_tls_policy_override_maps.cf socketmap:inet:postfix-tlspol:8642:QUERY
/opt/mailcow-dockerized/data/conf/postfix/main.cf:# smtp_tls_policy_maps =
Why does it work when adding smtp_tls_policy_maps = to data/conf/postfix/extra.cf? That makes absolutely no sense to me. I’m overseeing something?