Hello Mailcow community. I am trying to set up a Mailcow system on a home server, but incoming connections on port 25 from the external network appear to be being blocked within the Mailcow itself.
I am quite sure that it is not my ISP blocking the port as I have used wireshark running on my server to inspect the network traffic and can observe a SYN packet arriving into the system on port 25 when I send an email to my Mailcow domain from gmail:
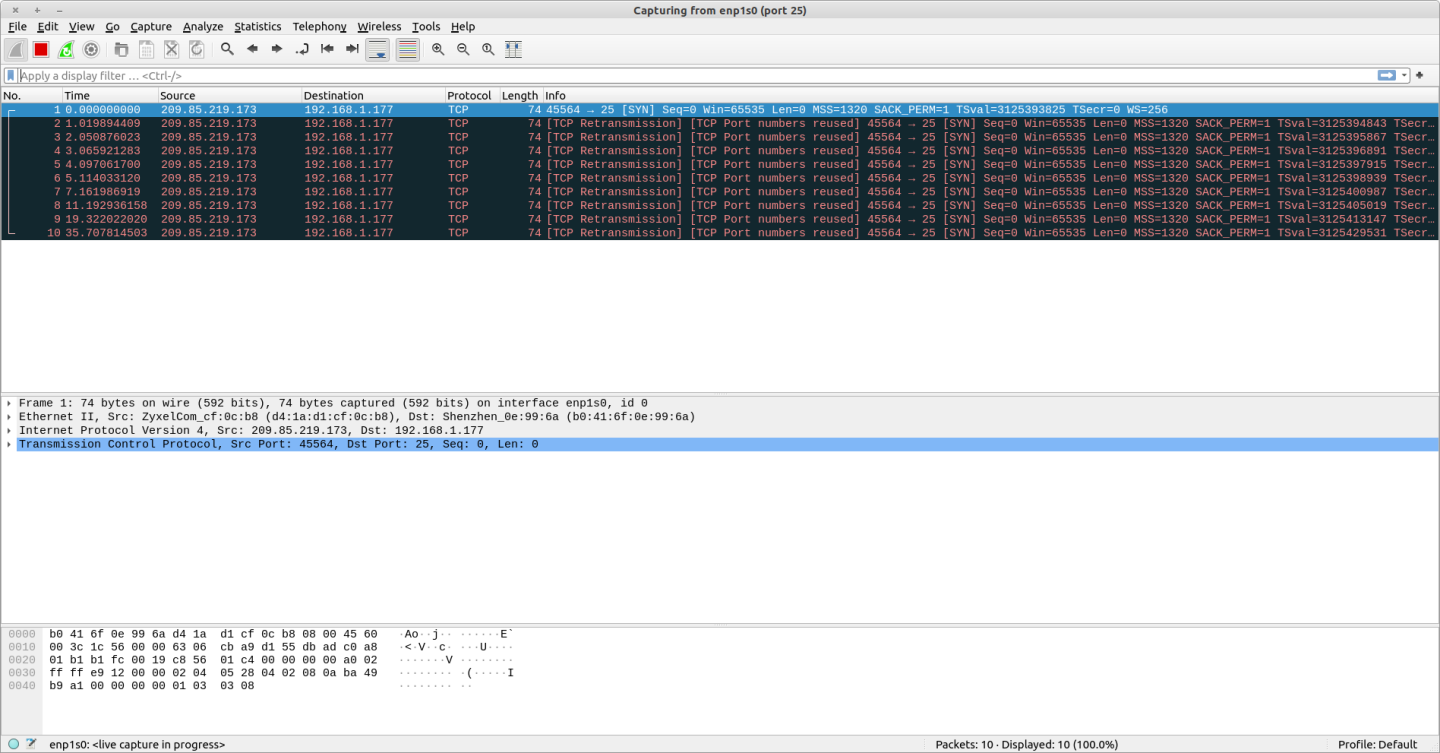
The wireshark trace shows the SYN arriving from 209.85.219.173, no ACK is returned, the SYN is retransmitted nine times by the external email server, all with no ACK being sent from the Mailcow server.
If I try making an incoming telnet connection on port 25 from an external network, I see a similar behaviour - see wireshark trace: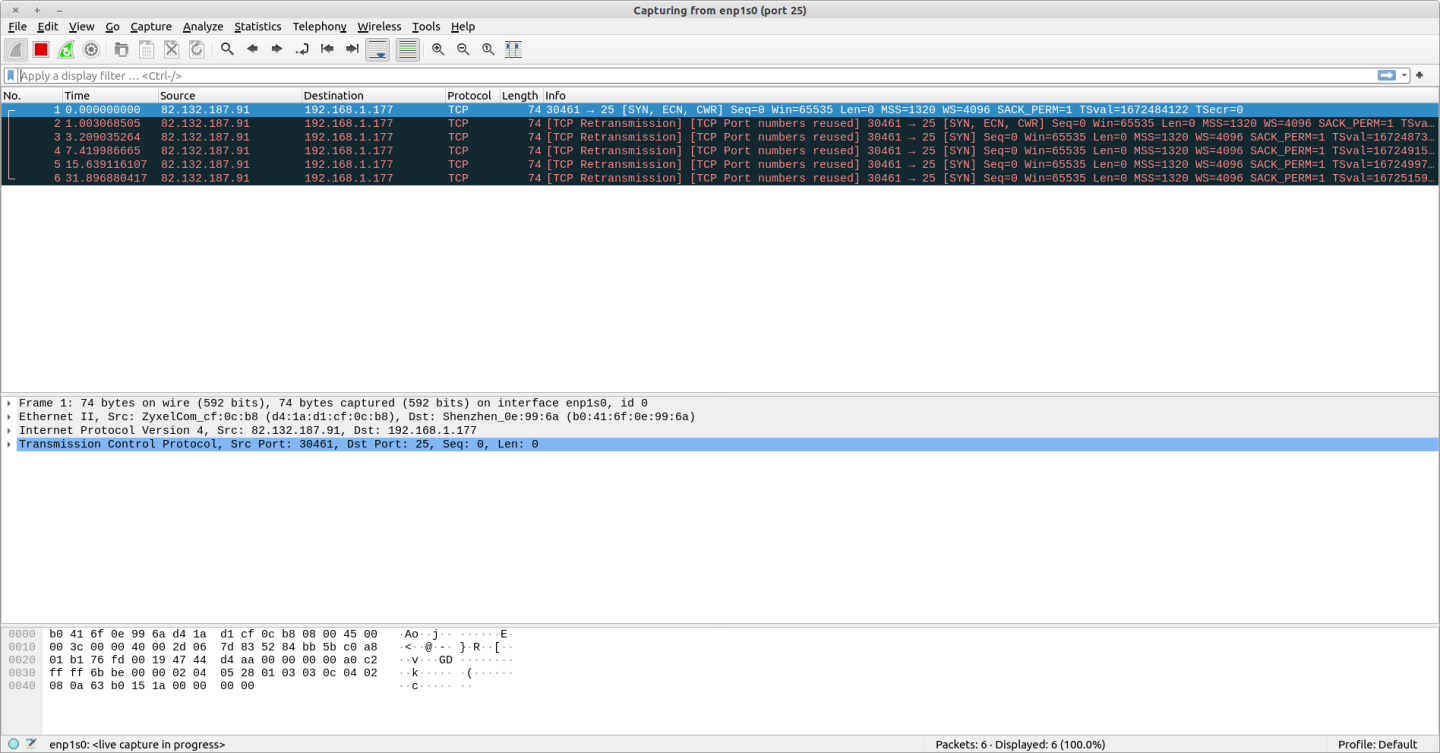
Making the telnet connection from a device on the local network I do get a connection - see trace: 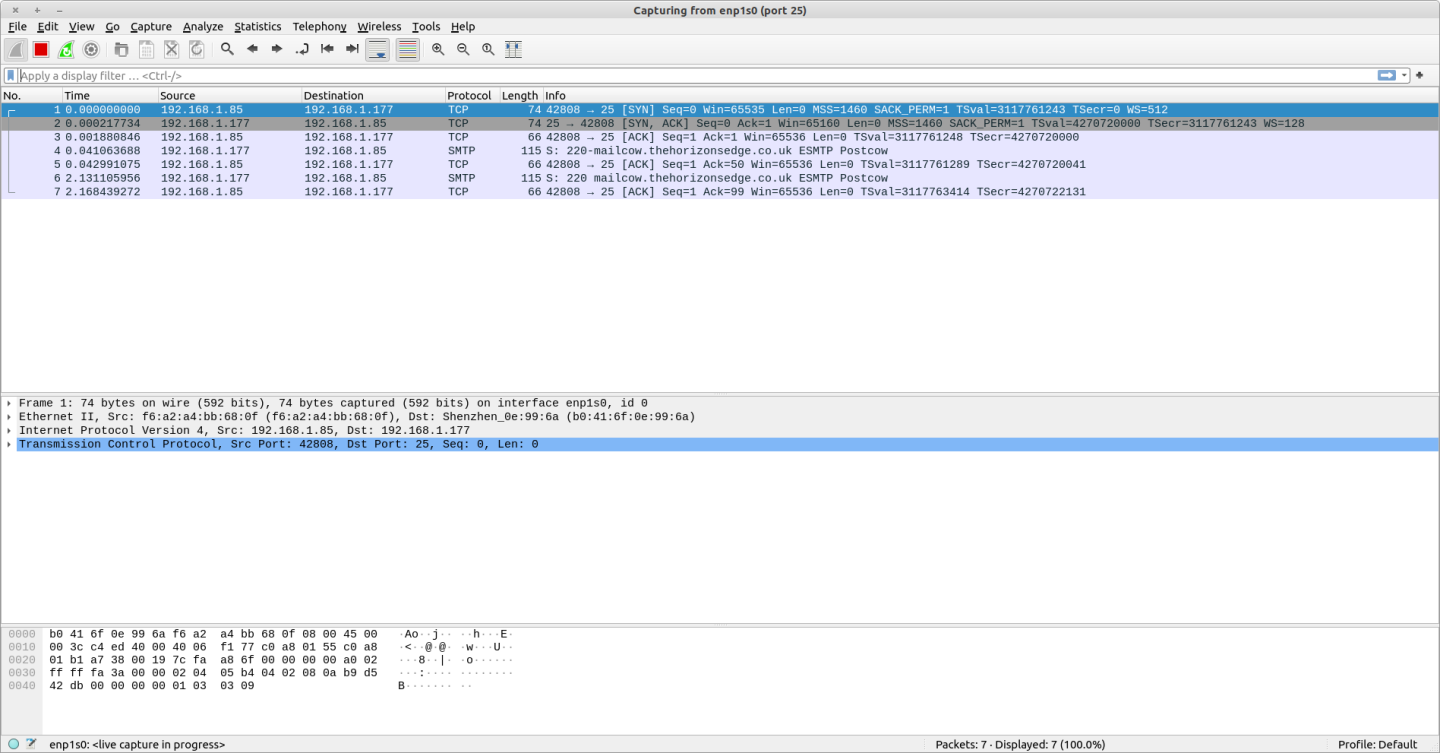
Hence it appears that the block is not caused by external filtering of port 25 by my ISP, but internal filtering dependent upon the originating IP address after the port 25 SYN has been received at my server ethernet interface.
For clarity, using SoGo (running locally either on my server, or on any other device on my local network) to send emails from my Mailcow server seems to work fine - I can send from my Mailcow domain to my gmail account with no problem, but sending replies back from gmail results in the behaviour of SYN’s arriving via my ISP on port 25, but no ACK’s being generated by the Mailcow server, as described above.
I am not aware of any origin-dependent block of port 25 being caused by my firewall.
Here is the listing of my iptables settings:
`root@horizon1:/opt/mailcow-dockerized# iptables -L
Chain INPUT (policy DROP)
target prot opt source destination
MAILCOW all – anywhere anywhere /* mailcow */
ufw-before-logging-input all – anywhere anywhere
ufw-before-input all – anywhere anywhere
ufw-after-input all – anywhere anywhere
ufw-after-logging-input all – anywhere anywhere
ufw-reject-input all – anywhere anywhere
ufw-track-input all – anywhere anywhere
Chain FORWARD (policy DROP)
target prot opt source destination
MAILCOW all – anywhere anywhere /* mailcow */
DOCKER-USER all – anywhere anywhere
DOCKER-ISOLATION-STAGE-1 all – anywhere anywhere
ACCEPT all – anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all – anywhere anywhere
ACCEPT all – anywhere anywhere
ACCEPT all – anywhere anywhere
ACCEPT all – anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all – anywhere anywhere
ACCEPT all – anywhere anywhere
ACCEPT all – anywhere anywhere
ACCEPT all – anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all – anywhere anywhere
ACCEPT all – anywhere anywhere
ACCEPT all – anywhere anywhere
ufw-before-logging-forward all – anywhere anywhere
ufw-before-forward all – anywhere anywhere
ufw-after-forward all – anywhere anywhere
ufw-after-logging-forward all – anywhere anywhere
ufw-reject-forward all – anywhere anywhere
ufw-track-forward all – anywhere anywhere
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ufw-before-logging-output all – anywhere anywhere
ufw-before-output all – anywhere anywhere
ufw-after-output all – anywhere anywhere
ufw-after-logging-output all – anywhere anywhere
ufw-reject-output all – anywhere anywhere
ufw-track-output all – anywhere anywhere
Chain DOCKER (3 references)
target prot opt source destination
ACCEPT tcp – anywhere 172.18.0.2 tcp dpt:8000
ACCEPT tcp – anywhere 172.22.1.249 tcp dpt:redis
ACCEPT tcp – anywhere 172.22.1.5 tcp dpt:8983
ACCEPT tcp – anywhere 172.22.1.6 tcp dpt:mysql
ACCEPT tcp – anywhere 172.22.1.250 tcp dpt:pop3
ACCEPT tcp – anywhere 172.22.1.250 tcp dpt:imap2
ACCEPT tcp – anywhere 172.22.1.250 tcp dpt:imaps
ACCEPT tcp – anywhere 172.22.1.250 tcp dpt:pop3s
ACCEPT tcp – anywhere 172.22.1.250 tcp dpt:sieve
ACCEPT tcp – anywhere 172.22.1.250 tcp dpt:12345
ACCEPT tcp – anywhere 172.22.1.253 tcp dpt:smtp
ACCEPT tcp – anywhere 172.22.1.253 tcp dpt:submissions
ACCEPT tcp – anywhere 172.22.1.253 tcp dpt:submission
ACCEPT tcp – anywhere 172.22.1.13 tcp dpt:45443
ACCEPT tcp – anywhere 172.22.1.13 tcp dpt:45480
Chain DOCKER-ISOLATION-STAGE-1 (1 references)
target prot opt source destination
DOCKER-ISOLATION-STAGE-2 all – anywhere anywhere
DOCKER-ISOLATION-STAGE-2 all – anywhere anywhere
DOCKER-ISOLATION-STAGE-2 all – anywhere anywhere
RETURN all – anywhere anywhere
Chain DOCKER-ISOLATION-STAGE-2 (3 references)
target prot opt source destination
DROP all – anywhere anywhere
DROP all – anywhere anywhere
DROP all – anywhere anywhere
RETURN all – anywhere anywhere
Chain DOCKER-USER (1 references)
target prot opt source destination
ufw-user-forward all – anywhere anywhere
RETURN all – 10.0.0.0/8 anywhere
RETURN all – 172.16.0.0/12 anywhere
RETURN all – 192.168.0.0/16 anywhere
RETURN udp – anywhere anywhere udp spt:domain dpts:1024:65535
ufw-docker-logging-deny tcp – anywhere 192.168.0.0/16 tcp flags:FIN,SYN,RST,ACK/SYN
ufw-docker-logging-deny tcp – anywhere 10.0.0.0/8 tcp flags:FIN,SYN,RST,ACK/SYN
ufw-docker-logging-deny tcp – anywhere 172.16.0.0/12 tcp flags:FIN,SYN,RST,ACK/SYN
ufw-docker-logging-deny udp – anywhere 192.168.0.0/16 udp dpts:0:32767
ufw-docker-logging-deny udp – anywhere 10.0.0.0/8 udp dpts:0:32767
ufw-docker-logging-deny udp – anywhere 172.16.0.0/12 udp dpts:0:32767
RETURN all – anywhere anywhere
Chain MAILCOW (2 references)
target prot opt source destination
DROP tcp – anywhere anywhere /* mailcow isolation */
Chain ufw-after-forward (1 references)
target prot opt source destination
Chain ufw-after-input (1 references)
target prot opt source destination
ufw-skip-to-policy-input udp – anywhere anywhere udp dpt:netbios-ns
ufw-skip-to-policy-input udp – anywhere anywhere udp dpt:netbios-dgm
ufw-skip-to-policy-input tcp – anywhere anywhere tcp dpt:netbios-ssn
ufw-skip-to-policy-input tcp – anywhere anywhere tcp dpt:microsoft-ds
ufw-skip-to-policy-input udp – anywhere anywhere udp dpt:bootps
ufw-skip-to-policy-input udp – anywhere anywhere udp dpt:bootpc
ufw-skip-to-policy-input all – anywhere anywhere ADDRTYPE match dst-type BROADCAST
Chain ufw-after-logging-forward (1 references)
target prot opt source destination
LOG all – anywhere anywhere limit: avg 3/min burst 10 LOG level warning prefix “[UFW BLOCK] ”
Chain ufw-after-logging-input (1 references)
target prot opt source destination
LOG all – anywhere anywhere limit: avg 3/min burst 10 LOG level warning prefix “[UFW BLOCK] ”
Chain ufw-after-logging-output (1 references)
target prot opt source destination
Chain ufw-after-output (1 references)
target prot opt source destination
Chain ufw-before-forward (1 references)
target prot opt source destination
ACCEPT all – anywhere anywhere ctstate RELATED,ESTABLISHED
ACCEPT icmp – anywhere anywhere icmp destination-unreachable
ACCEPT icmp – anywhere anywhere icmp time-exceeded
ACCEPT icmp – anywhere anywhere icmp parameter-problem
ACCEPT icmp – anywhere anywhere icmp echo-request
ufw-user-forward all – anywhere anywhere
Chain ufw-before-input (1 references)
target prot opt source destination
ACCEPT all – anywhere anywhere
ACCEPT all – anywhere anywhere ctstate RELATED,ESTABLISHED
ufw-logging-deny all – anywhere anywhere ctstate INVALID
DROP all – anywhere anywhere ctstate INVALID
ACCEPT icmp – anywhere anywhere icmp destination-unreachable
ACCEPT icmp – anywhere anywhere icmp time-exceeded
ACCEPT icmp – anywhere anywhere icmp parameter-problem
ACCEPT icmp – anywhere anywhere icmp echo-request
ACCEPT udp – anywhere anywhere udp spt:bootps dpt:bootpc
ufw-not-local all – anywhere anywhere
ACCEPT udp – anywhere mdns.mcast.net udp dpt:mdns
ACCEPT udp – anywhere 239.255.255.250 udp dpt:1900
ufw-user-input all – anywhere anywhere
Chain ufw-before-logging-forward (1 references)
target prot opt source destination
Chain ufw-before-logging-input (1 references)
target prot opt source destination
Chain ufw-before-logging-output (1 references)
target prot opt source destination
Chain ufw-before-output (1 references)
target prot opt source destination
ACCEPT all – anywhere anywhere
ACCEPT all – anywhere anywhere ctstate RELATED,ESTABLISHED
ufw-user-output all – anywhere anywhere
Chain ufw-docker-logging-deny (6 references)
target prot opt source destination
LOG all – anywhere anywhere limit: avg 3/min burst 10 LOG level warning prefix “[UFW DOCKER BLOCK] ”
DROP all – anywhere anywhere
Chain ufw-logging-allow (0 references)
target prot opt source destination
LOG all – anywhere anywhere limit: avg 3/min burst 10 LOG level warning prefix “[UFW ALLOW] ”
Chain ufw-logging-deny (2 references)
target prot opt source destination
RETURN all – anywhere anywhere ctstate INVALID limit: avg 3/min burst 10
LOG all – anywhere anywhere limit: avg 3/min burst 10 LOG level warning prefix “[UFW BLOCK] ”
Chain ufw-not-local (1 references)
target prot opt source destination
RETURN all – anywhere anywhere ADDRTYPE match dst-type LOCAL
RETURN all – anywhere anywhere ADDRTYPE match dst-type MULTICAST
RETURN all – anywhere anywhere ADDRTYPE match dst-type BROADCAST
ufw-logging-deny all – anywhere anywhere limit: avg 3/min burst 10
DROP all – anywhere anywhere
Chain ufw-reject-forward (1 references)
target prot opt source destination
Chain ufw-reject-input (1 references)
target prot opt source destination
Chain ufw-reject-output (1 references)
target prot opt source destination
Chain ufw-skip-to-policy-forward (0 references)
target prot opt source destination
DROP all – anywhere anywhere
Chain ufw-skip-to-policy-input (7 references)
target prot opt source destination
DROP all – anywhere anywhere
Chain ufw-skip-to-policy-output (0 references)
target prot opt source destination
ACCEPT all – anywhere anywhere
Chain ufw-track-forward (1 references)
target prot opt source destination
Chain ufw-track-input (1 references)
target prot opt source destination
Chain ufw-track-output (1 references)
target prot opt source destination
ACCEPT tcp – anywhere anywhere ctstate NEW
ACCEPT udp – anywhere anywhere ctstate NEW
Chain ufw-user-forward (2 references)
target prot opt source destination
Chain ufw-user-input (1 references)
target prot opt source destination
ACCEPT tcp – anywhere anywhere tcp dpt:45300
DROP tcp – anywhere anywhere tcp dpt:45200
ACCEPT tcp – anywhere anywhere tcp dpt:5900
ACCEPT udp – anywhere anywhere udp dpt:5900
ACCEPT tcp – anywhere anywhere tcp dpt:smtp
ACCEPT tcp – anywhere anywhere tcp dpt:pop3
ACCEPT tcp – anywhere anywhere tcp dpt:imap2
ACCEPT tcp – anywhere anywhere tcp dpt:submissions
ACCEPT tcp – anywhere anywhere tcp dpt:submission
ACCEPT tcp – anywhere anywhere tcp dpt:imaps
ACCEPT tcp – anywhere anywhere tcp dpt:pop3s
ACCEPT tcp – anywhere anywhere tcp dpt:sieve
ACCEPT udp – anywhere anywhere udp dpt:4190
ACCEPT tcp – anywhere anywhere multiport dports http,https
ACCEPT udp – anywhere anywhere multiport dports netbios-ns,netbios-dgm
ACCEPT tcp – anywhere anywhere multiport dports netbios-ssn,microsoft-ds
ACCEPT tcp – anywhere anywhere tcp dpt:ssh
Chain ufw-user-limit (0 references)
target prot opt source destination
LOG all – anywhere anywhere limit: avg 3/min burst 5 LOG level warning prefix “[UFW LIMIT BLOCK] ”
REJECT all – anywhere anywhere reject-with icmp-port-unreachable
Chain ufw-user-limit-accept (0 references)
target prot opt source destination
ACCEPT all – anywhere anywhere
Chain ufw-user-logging-forward (0 references)
target prot opt source destination
Chain ufw-user-logging-input (0 references)
target prot opt source destination
Chain ufw-user-logging-output (0 references)
target prot opt source destination
Chain ufw-user-output (1 references)
target prot opt source destination
ACCEPT tcp – anywhere anywhere tcp dpt:smtp
ACCEPT tcp – anywhere anywhere tcp dpt:pop3
ACCEPT tcp – anywhere anywhere tcp dpt:imap2
ACCEPT tcp – anywhere anywhere tcp dpt:submissions
ACCEPT tcp – anywhere anywhere tcp dpt:submission
ACCEPT tcp – anywhere anywhere tcp dpt:imaps
ACCEPT tcp – anywhere anywhere tcp dpt:pop3s
ACCEPT tcp – anywhere anywhere multiport dports http,https
ACCEPT udp – anywhere anywhere multiport dports netbios-ns,netbios-dgm
ACCEPT tcp – anywhere anywhere multiport dports netbios-ssn,microsoft-ds
root@horizon1:/opt/mailcow-dockerized#
`
I don’t recognise anything there that should be blocking the port 25 connection.
Also within the “Forwarding Hosts” table in the Mailcow UI, I have explicitly included the IP addresses of the gmail server and the external network telnet client, so these should not be subject to any blacklisting.
Is there some additional firewalling or IP blacklisting mechanism within Mailcow that I am not aware of?
Is there any mechanism for temporarily disabling all firewalling mechanisms within the Mailcow docker containers, and disabling all the address blacklisting features, so that I can try to diagnose where the fault is occuring?
I am aware of many other community postings here regarding port 25 being blocked, but they all seem to be a case of the external ISP doing the blocking. Where here my wireshark traces seem to show that the ISP is passing through the SYN request to open the port 25 connection, and the blockage is within my system, dependent upon the originating network IP.
Hoping that somebody can help please.