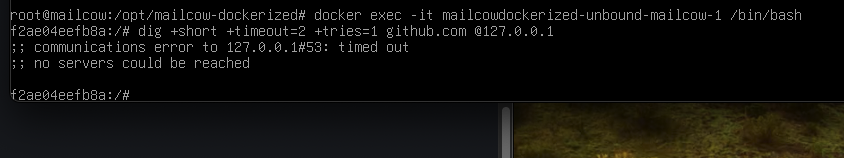
Must be the script.
Disabled the forward-zone. Did a docker compose down followed by a docker compose up -d. Entered the unbound container and altered the healthcheck.sh to 127.0.0.11. Did a docker compose restart unbound-mailcow.
[+] Restarting 1/1
 Container mailcowdockerized-unbound-mailcow-1 Started
Container mailcowdockerized-unbound-mailcow-1 Started
docker compose ps
mailcowdockerized-unbound-mailcow-1 mailcow/unbound:1.23 “/docker-entrypoint.…” unbound-mailcow 24 minutes ago Up 11 minutes (healthy) 53/tcp, 53/udp
I’ll define a forward-zone as workaround until this is fixed.