ok well call me paranoid, but if can restrict it I will. Also I want to disable pop3 and pops. do not see a reason in that. Now I am posting here my settings for failban and the current IP networks I am banning. and that is ridicilous. So for me it would be much easier to allow 1 IP address range and one public IP address. Furthermore yes Sogo looks nice but I only really need the mailboxes I have for several domains.
furthermore it seems that dovecot (intervals by -10 till to 0) and postfix (intervals by -2 till to 0) are falling ill (based on watchdog).
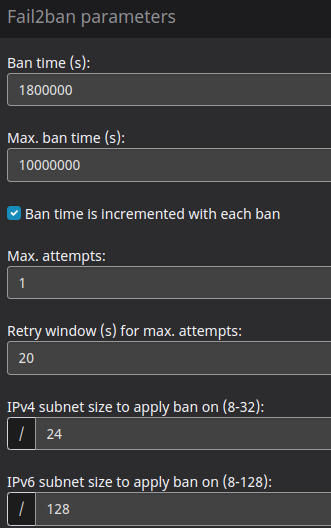
Those are the IP networks, which got “trapped” by failtoban and I checked manually (ip geolocations (always thread level = high and sometimes crawlers = yes) , whois and subnet calculator) and block them.
68.140.0.0/15
94.128.0.0/9
106.0.0.0/8
147.78.103.0/24
2.57.0.0/16
174.64.0.0/12
110.0.0.0/8
172.105.144.0/23
36.32.0.0/14
45.0.0.0/8
76.128.0.0/11
141.0.0.0/8
61.0.0.0/8
34.64.0.0/10
5.0.0.0/8
211.0.0.0/8
202.0.0.0/8
154.0.0.0/8
81.176.0.0/15
192.3.0.0/16
60.0.0.0/8
196.191.0.0/16
188.162.0.0/16
76.96.0.0/11
185.0.0.0/8
187.0.0.0/8
173.73.0.0/16
172.105.0.0/17
62.97.32.0/19
190.200.0.0/13
103.0.0.0/8
62.16.96.0/19
112.0.0.0/5
87.120.84.0/24
178.176.0.0/14
80.16.0.0/13
1.0.0.0/8
64.62.128.0/17
120.0.0.0/5
176.32.0.0/11
41.0.0.0/8
38.0.0.0/8
89.154.0.0/16
208.0.0.0/8
39.32.0.0/11
102.37.0.0/16
192.72.0.0/19
2.55.0.0/16
14.0.0.0/8
167.94.138.0/24
91.72.0.0/14
172.104.0.0/16
221.0.0.0/8
2.64.0.0/13
39.128.0.0/10
92.36.0.0/16
220.0.0.0/8
193.187.82.0/23
182.0.0.0/8
85.31.45.0/24
68.128.0.0/13
222.0.0.0/8
201.0.0.0/8
190.119.0.0/16
109.48.0.0/15
172.105.146.0/24
68.136.0.0/14
189.8.124.0/22
149.72.0.0/16
46.0.0.0/8
139.0.0.0/8
219.0.0.0/8
191.36.0.0/16
218.0.0.0/8
85.15.128.0/18
171.208.0.0/12
186.0.0.0/8
111.0.0.0/8
81.161.229.0/24
198.23.128.0/17
144.48.0.0/16
58.0.0.0/8
59.0.0.0/8
81.86.0.0/16
136.255.0.0/16
50.128.0.0/9
223.0.0.0/8
192.237.0.0/16
172.105.128.0/20
[unknown]
The IP address range is indeed a 10.x.x.x and I have one static IP that seems never changing, which actually would not be an issue because I would prefer going through the 10.x.x.x network. The mailserver I have is on a VPS by a provider.
I would add those nginx config setting in the nginx.conf? I am not so familiar with webserver configs.
[unknown]
The IP address range is indeed a 10.x.x.x and I have one static IP that seems never changing, which actually would not be an issue because I would prefer going through the 10.x.x.x network. The mailserver I have is on a VPS by a provider.
I would add those nginx config setting in the nginx.conf? I am not so familiar with webserver configs.
[unknown] The IP address range is indeed a 10.x.x.x and I have one static IP that seems never changing, which actually would not be an issue because I would prefer going through the 10.x.x.x network. The mailserver I have is on a VPS by a provider.
I would add those nginx config setting in the nginx.conf? I am not so familiar with webserver configs.
The IP address range is indeed a 10.x.x.x and I have one static IP that seems never changing, which actually would not be an issue because I would prefer going through the 10.x.x.x network. The mailserver I have is on a VPS by a provider.
I would add those nginx config setting in the nginx.conf? I am not so familiar with webserver configs.
[unknown]
The IP address range is indeed a 10.x.x.x and I have one static IP that seems never changing, which actually would not be an issue because I would prefer going through the 10.x.x.x network. The mailserver I have is on a VPS by a provider.
I would add those nginx config setting in the nginx.conf? I am not so familiar with webserver configs.
[unknown]
The IP address range is indeed a 10.x.x.x and I have one static IP that seems never changing, which actually would not be an issue because I would prefer going through the 10.x.x.x network. The mailserver I have is on a VPS by a provider.
I would add those nginx config setting in the nginx.conf? I am not so familiar with webserver configs.
[unknown]
The IP address range is indeed a 10.x.x.x and I have one static IP that seems never changing, which actually would not be an issue because I would prefer going through the 10.x.x.x network. The mailserver I have is on a VPS by a provider.
I would add those nginx config setting in the nginx.conf? I am not so familiar with webserver configs.